Keeping that private stuff under wraps has never been more critical than now, in this digital era we find ourselves in. Cybersecurity threats have become increasingly sophisticated as time has passed, becoming a significant hazard for people like you, me, businesses, and even governments. Now that technology is advancing at a seemingly unattainable rate, the same can be said for tactics used by cybercriminals. Therefore, organizations must stay one step ahead of them all with solid security measures.
Common Types of Cybersecurity Threats:
Cybercriminals have many tricks up their sleeves when accessing data without consent. One of those underhanded tactics is phishing. Phishing is when someone poses as an entity that’s trustworthy through email or a fake website to trick people into giving away their personal information, like usernames, passwords, and credit card details.
Another threat that’s proliferating is malware infection. By hearing the word “malware,” I’m sure you can get an idea of their intentions. Bad ones. These malicious software programs are designed to ruin your computer system by gaining unauthorized access to it, or worse. They come in the form of viruses, worms, trojans, ransomware, or spyware, which can steal your sensitive files if infected.
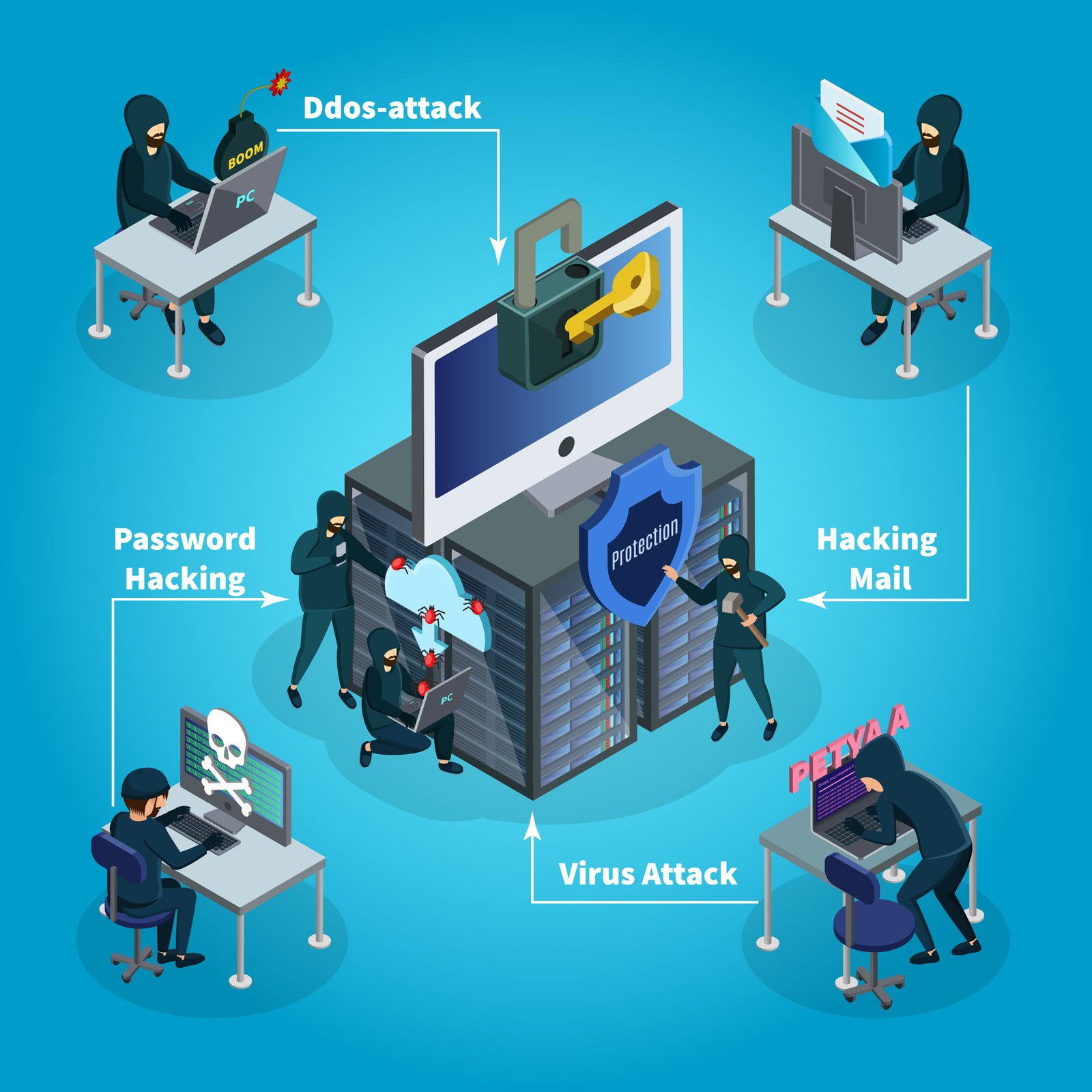
Last but certainly not least on our list are data breaches, which rightfully worry businesses and individuals alike. These usually happen when bad actors gain access to someone else’s classified information from another organization without permission. Breaches like this often expose personal information, such as financial records or trade secrets, that should never see the light of day. This could cost you dearly due to reputation damage and legal implications.
Impact of Cybersecurity Threats on Businesses:
The impact of data breaches doesn’t stop at immediate financial losses; companies might also experience irreparable reputational damage. When a breach occurs, trust is broken between a business and its customers/clients. When trust goes out the window, so does loyalty.
The cost of picking up the pieces after an incident like this could be astronomical for some organizations. In order to prevent future breaches, multiple things must be done, which include enhanced security measures, forensic investigations, and legal support. Failure to comply with data protection regulations could also slap businesses with regulatory fines.
On top of that, a successful cyberattack will likely leave these organizations in shambles because it can disrupt business operations, causing productivity and financial losses.
The Importance of Data Protection:
While it’s good to know about all these threats, that doesn’t mean you should go around being paranoid about them. Instead, we’d recommend focusing on how to protect your data from being stolen or destroyed entirely. This is important regardless of whether it’s personal information or intellectual property, because no matter what it is, keeping whatever you own private is vital for privacy reasons.
Now let’s say you’re running a company, and that company handles customer information. Your level of responsibility skyrockets tenfold when entrusted with someone else’s data. Not properly protecting other people’s stuff will result in lawsuits, financial penalties, and, worst-case scenario, the loss of customers.
Moreover, even if you don’t have customers or clients who entrust you with their personal information every day, people still expect their own data to be handled securely online, as they should! A single slip-up could lead to a loss of business and reputation damage.
Best Practices for Data Protection:
Organizations and individuals need to understand best practices for data protection to protect their sensitive data and reduce the threat of cybersecurity attacks. By following these measures, they can significantly lessen their chances of falling victim to a cyberattack.
Secure Passwords and Authentication Systems
Strong passwords are one of the most basic forms of data protection. Weak passwords can be easily cracked by hackers, giving them immediate access to private information. It is suggested that people use a mixture of upper- and lower-case letters, numbers, and special characters when creating passwords. In addition, they should avoid reusing passwords across different accounts and change them regularly.
Two-factor authentication (2FA) adds an extra layer of security in addition to users’ passwords. This method requires users to provide some form of additional verification beyond their original password, such as a fingerprint scan or unique code sent through their mobile device. Even if your password has been compromised, this method will make it extremely difficult for someone to gain unauthorized access.
Regular Updates for Software and Systems
Updated software is crucial in preventing cybersecurity threats. Oftentimes, software updates will include patches that close vulnerabilities that hackers could exploit. Failure to update software leaves systems at risk.
It is important that operating systems, web browsers, antivirus software, and any other applications used on computers or mobile devices are all consistently updated. By doing so, organizations can ensure that they have the latest security enhancements, which reduce the risk of falling victim to an attack.
Educating Employees about Cybersecurity Best Practices
Human error is one of the top causes behind cybersecurity breaches. Educating employees about cybersecurity best practices can help prevent future incidents from occurring. Employees should learn how to identify phishing attempts and how to properly report them. Additionally, it’s necessary for people to understand why strong passwords are so important, as well as what risks come with visiting suspicious websites or downloading attachments from unknown sources.
Security awareness training needs to be conducted regularly in order for employees to stay informed about the most recent threats and preventative measures. By creating a culture of cybersecurity awareness, organizations will greatly reduce the odds of a successful cyberattack.
Encryption and Secure Communication Channels
Encrypting sensitive data is an extremely effective way to protect it from unauthorized access. Once encrypted, data becomes scrambled into an unreadable format that can only be deciphered with the correct decryption key. Even if this information is intercepted, it will remain secure and unintelligible to hackers.
Using secure communication channels, such as virtual private networks (VPNs) and encrypted messaging apps, adds yet another layer of protection. VPNs create a connection between devices and the internet that encrypts all transmitted data. As for encrypted messaging apps, they safeguard conversations by encrypting them end-to-end, allowing only intended recipients to view messages.
Conclusion: Tackling Data Protection Head-on
The importance of cybersecurity cannot be overstated in today’s interconnected world. Cybercriminals are constantly developing new tactics so organizations must make sure they’re implementing strong security measures consistently.
If there is one thing we all can agree on, it’s that your data is important. By understanding the different types of threats out there and how they could impact a business, individuals and organizations alike will be equipped with the knowledge they need to keep their information safe. From using strong passwords to regularly updating software, there are plenty of best practices that can help you avoid falling victim to an attack.
At the end of the day, businesses and individuals must remember that staying informed about cybersecurity risks and learning ways to stay secure should always be a top priority. If your sensitive data falls into the wrong hands, you could be looking at financial loss, damaged reputation, and even worse — invasion of privacy.

